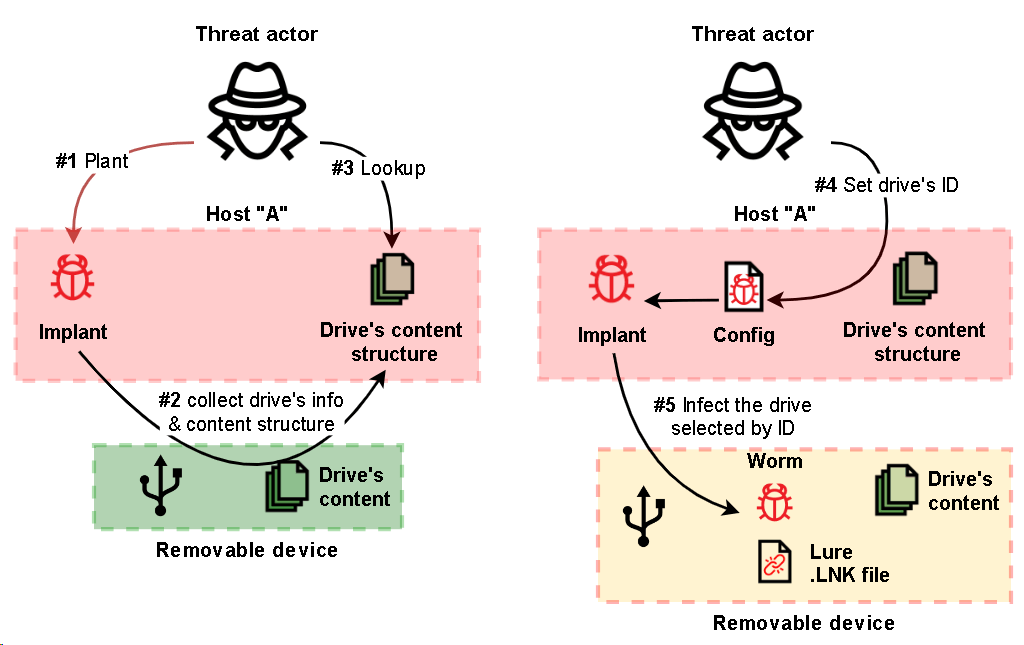
Top Threat Actors TTPs
1. Nation-State Threat Actors
These groups are often state-sponsored and target governments, infrastructure, and large enterprises.
- APT29 (Cozy Bear – Russia)
- Tactics: Initial access, persistence, credential access
- Techniques: Spear-phishing, stolen credentials, DLL side-loading
- Procedures: Leveraging legitimate services for command and control (C2), slow and stealthy data exfiltration
- APT28 (Fancy Bear – Russia)
- Tactics: Credential access, execution, exfiltration
- Techniques: Brute force, malware implants, PowerShell scripts
- Procedures: Targeting political organizations and using zero-day exploits
- Lazarus Group (North Korea)
- Tactics: Resource development, initial access, collection
- Techniques: Supply chain attacks, watering hole attacks, cryptocurrency theft
- Procedures: Custom malware development and highly destructive payloads
- APT41 (China)
- Tactics: Privilege escalation, lateral movement, exfiltration
- Techniques: Exploiting web-facing applications, remote access tools (RATs)
- Procedures: Blending cyber espionage with financial crime
2. Cybercriminal Groups
These actors are financially motivated, targeting organizations and individuals for ransom, theft, or fraud.
- Conti Ransomware Group
- Tactics: Impact, data encryption, defense evasion
- Techniques: RDP brute force, Cobalt Strike for lateral movement
- Procedures: Double extortion — encrypting data and threatening to leak it
- LockBit
- Tactics: Discovery, execution, exfiltration
- Techniques: Phishing, exploiting public-facing apps, file encryption
- Procedures: Using custom-built ransomware to quickly encrypt networks
- FIN7
- Tactics: Persistence, collection, command and control
- Techniques: Spear-phishing, script-based attacks, credential dumping
- Procedures: Targeting point-of-sale systems for financial theft
3. Hacktivist Groups
These actors are motivated by ideology or political goals, often targeting organizations to make a public statement.
- Anonymous
- Tactics: Initial access, impact, availability disruption
- Techniques: DDoS attacks, website defacement, information leaks
- Procedures: Leveraging social media and public platforms for coordination
- LulzSec (historical but relevant for CEH)
- Tactics: Reconnaissance, discovery, impact
- Techniques: SQL injection, exploiting known vulnerabilities
- Procedures: High-publicity attacks for “lulz” or chaos
📚 Mapping TTPs to MITRE ATT&CK
The MITRE ATT&CK framework is a goldmine for learning real-world TTPs. For your CEH studies, get familiar with how attackers progress through the attack lifecycle:
Reconnaissance → Resource Development → Initial Access → Execution → Persistence → Privilege Escalation → Defense Evasion → Credential Access → Discovery → Lateral Movement → Collection → Exfiltration → Impact