TCP handshake and TLS handshake
Attackers often abuse legitimate communication protocols like the TCP handshake and TLS handshake to establish secure connections for malicious activities. Here’s how they use these mechanisms:
1. TCP Handshake Abuse
The TCP handshake establishes a reliable communication channel, consisting of:
- SYN (Synchronize): The client sends a request to initiate communication.
- SYN-ACK (Synchronize-Acknowledge): The server acknowledges the request.
- ACK (Acknowledge): The client completes the handshake.
Attack Scenarios:
- Command and Control (C2) Channels: Attackers use the handshake to initiate communication with compromised systems while ensuring reliable data transmission.
- SYN Flood Attacks: Exploit incomplete handshakes to overload servers.
- Evasion Techniques: Blend malicious communication within legitimate TCP traffic, making detection harder.
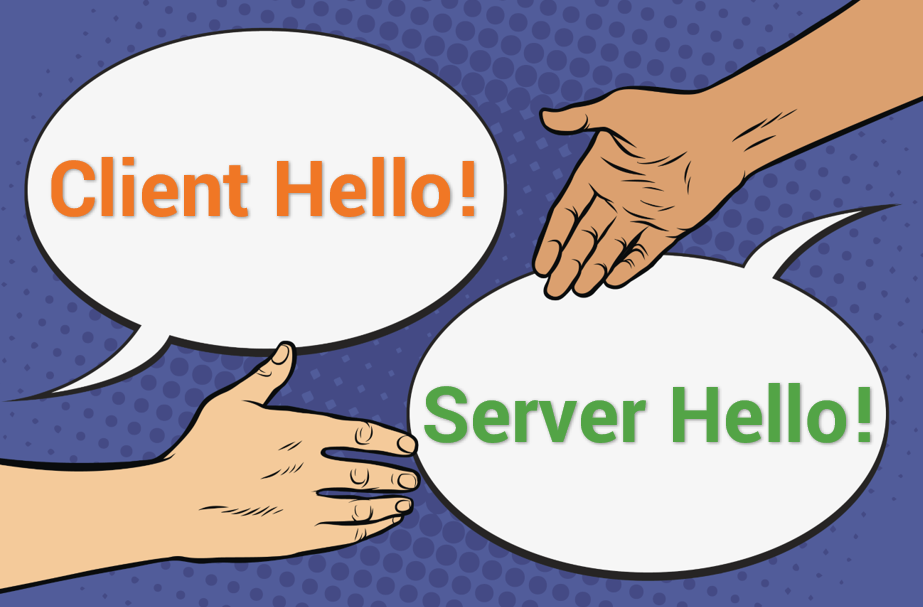
2. TLS Handshake with Certificate Exchange
The TLS handshake secures the communication channel using encryption. It includes:
- Negotiating security parameters (TLS version, cipher suite).
- Exchanging certificates to verify identities.
- Establishing a shared session key for encryption.
Attack Scenarios:
- Encrypted Malware Delivery: Attackers use TLS to encrypt malware communication, hiding it from security tools that don’t inspect encrypted traffic.
- Phishing Sites: Attackers deploy certificates on malicious sites to appear legitimate (e.g., “secure” padlock).
- C2 Servers: TLS is used for encrypted communication between malware and attackers, bypassing detection systems.
- Man-in-the-Middle (MitM): Compromised TLS communication is used to intercept and manipulate traffic.
How These Are Exploited Together
- Initial Connection:
- A malicious client initiates a TCP handshake with a target server or vice versa.
- It then establishes a secure TLS channel to encrypt traffic.
- Data Exfiltration or Malware Command:
- Encrypted channels are used to send stolen data or receive commands without detection.
- Avoiding Detection:
- By mimicking legitimate traffic patterns (e.g., web browsing or API calls), attackers bypass many security tools that don’t inspect encrypted traffic deeply.
Mitigation Strategies
- Network Traffic Monitoring: Analyze TCP and TLS traffic patterns for anomalies.
- TLS Inspection: Implement SSL/TLS decryption for deep packet inspection (DPI).
- Certificate Validation: Use Certificate Transparency logs to detect suspicious or malicious certificates.
- Behavior Analysis: Monitor behavior post-handshake, like unusual data transfer or communication with known malicious IPs.
- Threat Intelligence: Use updated threat intelligence to identify malicious C2 servers or suspicious domains.