THREAT HUNTING 101 A Comprehensive eGuide
Original price was: ₹20.00.₹15.00Current price is: ₹15.00.
Description
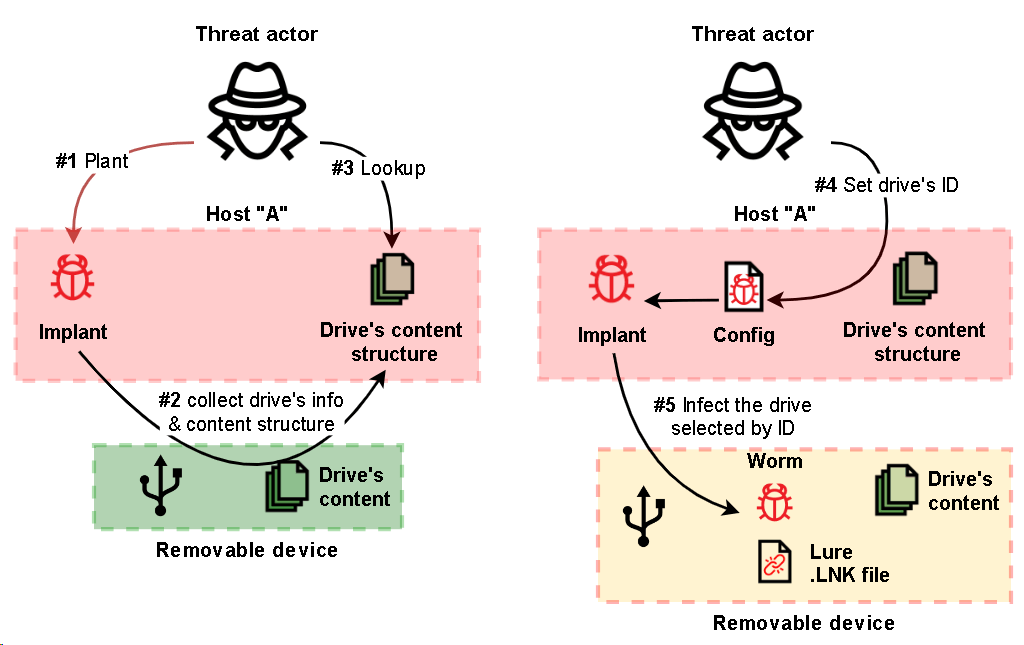
Advanced threat actors can bypass the initial security measures implemented by organizations. These malicious entities often linger within networks for months, leveraging confidential data or stolen login credentials to move laterally across the environment. To detect such hidden cyber threats, security analysts employ threat hunting—a proactive process aimed at uncovering anomalies within an organization’s infrastructure. This critical aspect of a strong cyber defense strategy integrates proactive methodologies, advanced technology, and threat intelligence to intercept attacks before they can breach an organization’s defenses.











Reviews
There are no reviews yet.