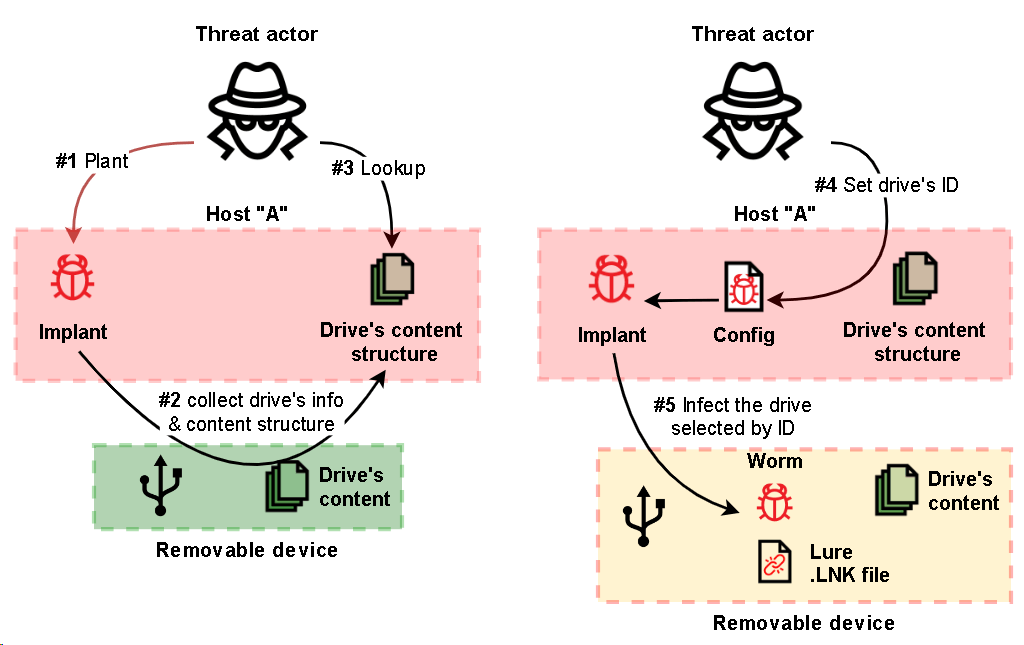
Challenges in SOC
Challenges in a Security Operations Center (SOC) can be grouped into several categories, as they stem from operational, technical, organizational, and resource-related issues. Here are the key challenges faced by SOC teams:
1. Alert Overload
- Volume of Alerts: SOC teams often face an overwhelming number of alerts, many of which are false positives. This can lead to “alert fatigue,” where critical threats might be overlooked.
- Prioritization: Identifying which alerts are most critical and require immediate attention is often difficult without automated tools and clear processes.
2. Lack of Skilled Personnel
- Skill Gap: The demand for skilled cybersecurity professionals far exceeds the supply, making it challenging to staff a SOC with experienced analysts.
- Training: Keeping up with the ever-evolving threat landscape requires continuous training, which can be resource-intensive.
3. Evolving Threat Landscape
- Sophisticated Attacks: Cybercriminals constantly develop new tactics, techniques, and procedures (TTPs), making it difficult for SOC teams to stay ahead.
- Advanced Persistent Threats (APTs): Long-term, targeted attacks can be challenging to detect and mitigate.
4. Lack of Automation
- Manual Processes: Many SOCs still rely on manual processes, which are time-consuming and inefficient.
- Integration of Tools: Automating tasks with Security Orchestration, Automation, and Response (SOAR) tools can be complex, especially if existing tools aren’t interoperable.
5. Insufficient Visibility
- Blind Spots: SOCs often lack full visibility into networks, endpoints, cloud environments, and third-party integrations, which leaves gaps for attackers to exploit.
- Data Overload: Collecting and managing data from multiple sources without proper correlation tools can lead to blind spots.
6. Incident Response Challenges
- Time to Respond: Delays in detecting and responding to incidents can result in significant damage.
- Coordination: Poor communication between teams or lack of predefined playbooks can hinder the response process.
7. Budget and Resource Constraints
- Limited Funding: Many organizations struggle to allocate sufficient budgets for SOC operations, affecting staffing, tools, and training.
- Tool Costs: High costs of security tools, licenses, and subscriptions can be a barrier.
8. Compliance and Regulation
- Complex Requirements: Adhering to various compliance standards (e.g., GDPR, PCI DSS, HIPAA) requires meticulous monitoring and reporting.
- Audits: Preparing for and undergoing regular security audits can strain resources.
9. Insider Threats
- Malicious Insiders: Employees or contractors with malicious intent can bypass traditional defenses.
- Unintentional Errors: Mistakes made by employees, such as misconfigurations or falling victim to phishing, can also pose significant risks.
10. Tool Sprawl
- Too Many Tools: Organizations often deploy numerous security tools, leading to complexity in managing and integrating them.
- Inefficiency: Lack of centralized management can lead to inefficiencies and missed opportunities for threat detection.
11. Burnout and Stress
- High Pressure: The 24/7 nature of SOC operations and constant exposure to high-stakes incidents can lead to analyst burnout.
- Retention Issues: Stress and dissatisfaction often result in high turnover rates among SOC staff.
12. Threat Intelligence Integration
- Relevance: Not all threat intelligence feeds are actionable or relevant to the organization’s context.
- Timeliness: Delayed or outdated threat intelligence can render it ineffective.
13. Cloud and Hybrid Environments
- Complexity: Monitoring hybrid and multi-cloud environments adds layers of complexity to threat detection.
- Cloud-Specific Threats: SOCs may lack tools or expertise to address threats specific to cloud environments.
14. Data Privacy Concerns
- Ethical Considerations: Balancing security monitoring with employee privacy can be challenging.
- Regulatory Scrutiny: Ensuring that monitoring tools comply with data privacy laws is essential.
15. Supply Chain Risks
- Third-Party Vulnerabilities: A breach in a partner or vendor’s network can expose the organization to risks.
- Monitoring Limitations: Visibility into third-party systems is often limited.
Mitigating SOC Challenges
To overcome these challenges, organizations can:
Outsource or Co-Manage SOC: Partner with Managed Security Service Providers (MSSPs) if internal capabilities are limited.
Invest in Automation: Leverage SOAR and AI tools for automated threat detection and response.
Continuous Training: Upskill SOC analysts with the latest training in cybersecurity trends and tools.
Threat Hunting: Implement proactive threat-hunting processes to identify risks before they escalate.
Centralize Monitoring: Adopt Security Information and Event Management (SIEM) solutions for better visibility and correlation.
Improve Processes: Develop clear incident response playbooks and prioritize effective communication.