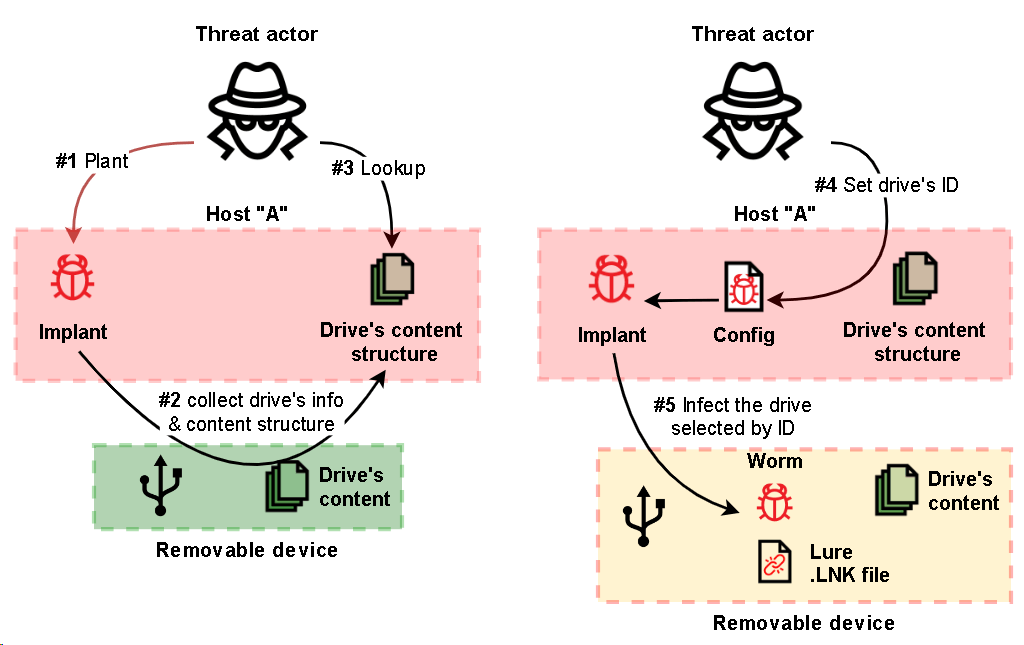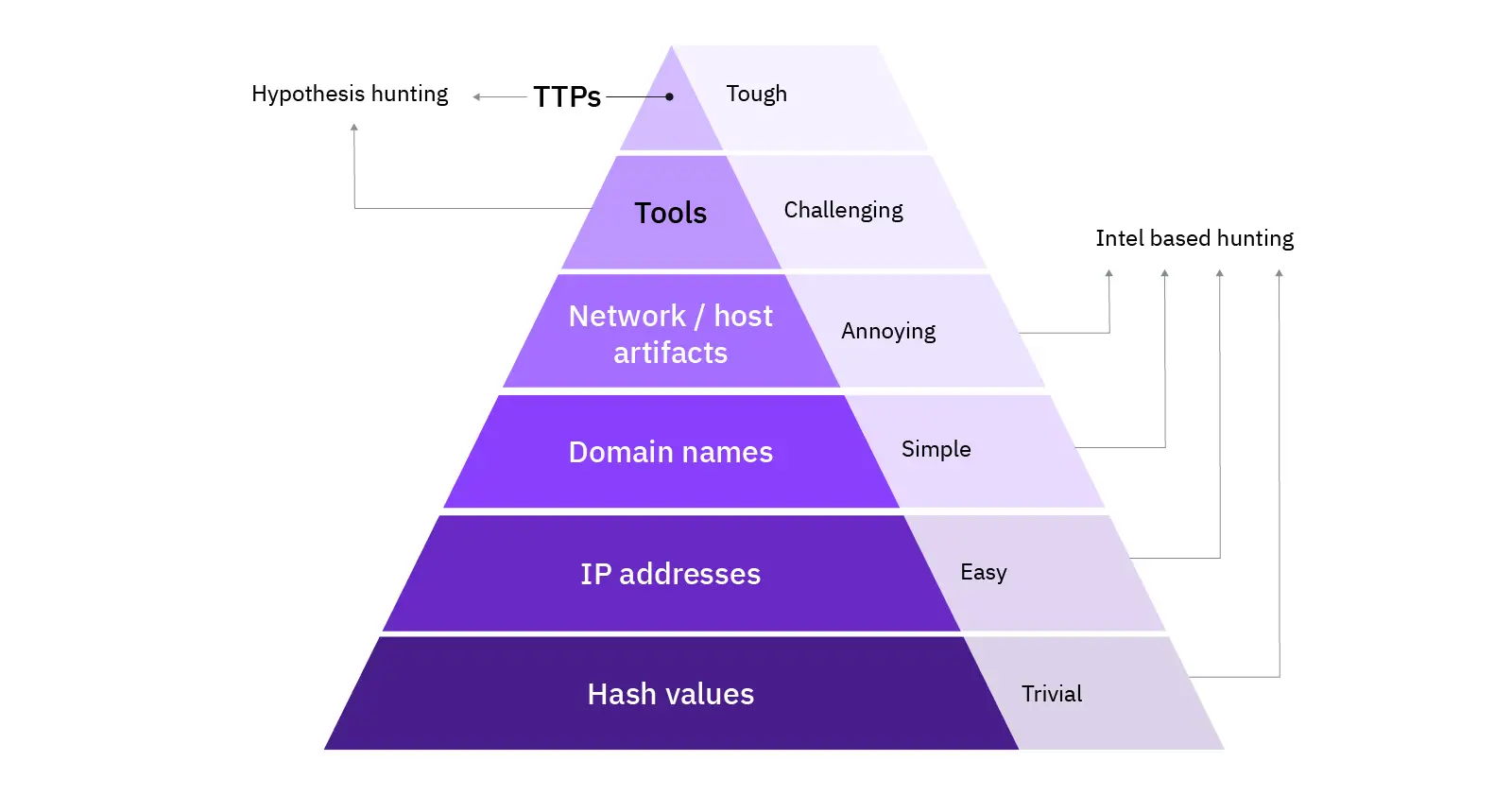
Challenges In Threat Hunting
The ever-evolving landscape of cyber threats continuously refines its attack strategies, bypassing traditional defense mechanisms and remaining undetected until its objectives are achieved. In response to these stealthy threats, threat hunting has emerged as a vital proactive defense strategy against sophisticated and concealed cyber adversaries. However, despite its importance, there is still a limited understanding of the best practices and challenges involved in effective threat hunting.
To bridge this gap, we conducted semi-structured interviews with 22 experienced threat hunters to explore their daily practices, challenges, and strategies for overcoming obstacles. Our findings reveal that threat hunters employ a diverse range of approaches, often combining multiple methods. They emphasize that maintaining flexibility in their techniques enhances their ability to detect subtle threat indicators that might otherwise go unnoticed with a single approach. Their challenges span technical issues as well as organizational and cultural barriers.
Based on these insights, we offer empirical recommendations to enhance threat-hunting best practices.
Threat hunting is a proactive cyber security approach, but it comes with several challenges, including:
- Large Data Volume – Security teams must sift through massive amounts of data to identify threats, which can be time-consuming and complex.
- Advanced and Evasive Threats – Attackers use sophisticated techniques like fileless malware and polymorphic viruses to evade detection.
- Lack of Skilled Personnel – Effective threat hunting requires highly skilled analysts, but there is a shortage of experienced professionals.
- False Positives – Identifying real threats among numerous alerts can be difficult, leading to wasted time and resources.
- Integration with Existing Tools – Ensuring seamless collaboration between threat-hunting platforms and existing security infrastructure is challenging.
- Threat Intelligence Gaps – Incomplete or outdated threat intelligence can hinder accurate detection and response.
- Real-Time Detection and Response – Quickly detecting and mitigating threats before they cause damage is a constant struggle.
- Evolving Attack Techniques – Cybercriminals continuously adapt their methods, making it harder to keep up with new threats.
Overcoming these challenges requires a combination of advanced tools, continuous learning, and a proactive security mind-set.